On December 1, the Standard 2.0 for Network Security Level Protection System (hereinafter referred to as "Equal Security 2.0") was formally implemented, and in accordance with Article 21 of the "Network Security Law": Network operators shall implement Security protection obligations to protect the network from interference, damage, or unauthorized access, and to prevent network data from being leaked or stolen or tampered with.
Therefore, network operators need to implement network security level protection in accordance with the Equal Guarantee 2.0 requirements, and carry out the entire process related to them: rating, filing, overall planning, design and implementation, operation and maintenance, and termination. Among them, grading and filing are the beginning and foundation of the implementation of equal guarantees.
Grading and filing process
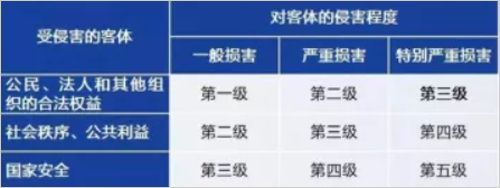
The rank protection system is very important. The equal guarantee 2.0 is similar to the equal guarantee 1.0. According to the degree of importance, the information system is divided into 5 levels. Different levels implement different standards of protection standards and record them. For enterprises, grading and filing are very important steps, so that companies can clarify the protection standards they should implement. If the level is not clear, the implementation of protection standards below the rating will fall into an illegal situation. If the protection standards are higher than the rating, Will waste costs.
The grading and filing process is divided into four steps: grading, object analysis, level determination, and filing. It involves all roles in the implementation of equal guarantees, including operating units, network security companies, competent departments, network information offices, network security assessment agencies, Network security service agencies and public security agencies.
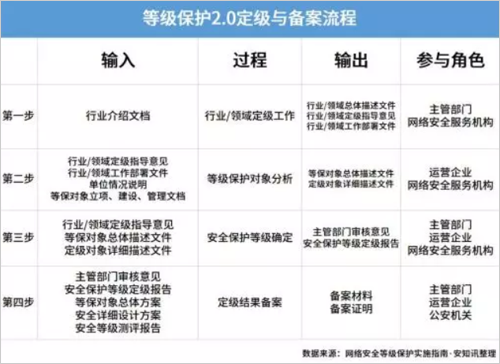
First, industry authorities and network security service agencies determine the level of insurance in their industry, and complete the industry / sector grading work. Second, the operating unit and network security service agency complete the protection according to the industry, business scope, product role, etc. Object importance analysis and expert review; the third step is the competent authority to review and approve the equal guarantee objects and rating to determine the number and grade of equal guarantee objects; finally, according to the requirements of the equal insurance management department, go through the filing procedures and report Public security organs carry out record review and complete all grading and record work.
It should be noted here that in addition to the first-level guarantee, no classification is required, and the remaining levels need to be declared and filed. The third-level guarantee is the highest level of national certification for non-bank institutions and belongs to the "supervisory level." "The supervision and inspection by the national information security supervision department is the current level that financial payment institutions and enterprises need to achieve.
Evaluation exists in all aspects of implementation
Evaluation is an important part in the implementation of equal guarantee. Its main role is to detect and assess whether the safety level of the rated object meets the basic requirements of the corresponding level. It is an important means to implement equal guarantee. The unit needs to establish a concept: evaluation is not a separate link, and it is not a one-time pass for peace of mind. As long as the implementation of the guarantee, the evaluation will always exist.
Institutions that can conduct evaluations must have corresponding qualifications. During the evaluations, they must obtain the entrustment of the operating and user units or the authorization of the insurance management department. The operating and using units conduct status analysis through registration assessment, determine the current status and problems of system security protection, and determine the system's rectification needs.
In the process of grading, construction and operation and maintenance of iso-guarantees, evaluation work is required to obtain an evaluation report. According to the regulations, the third-level equal guarantee object needs to be evaluated once a year. The evaluation report is an important basis for carrying out rectification and reinforcement, and it is also an important attachment for the record of the third-level and higher-level objects. Importance in the process.
Some people call the process of waiting for insurance implementation to be a process of evaluation, rectification, and re-evaluation, and then rectification until it passes the evaluation. The assessment content of the third-level certification needs to cover the five levels of security technology requirements and five levels of security management requirements. It mainly includes nearly 300 requirements including information protection, security audits, and communication confidentiality. They involve a total of test scores. Class 73, the specific requirements can refer to "Information Security Technology Network Security Level Protection Evaluation Requirements", and the evaluation process can refer to "Information Security Technology Network Security Level Protection Evaluation Process Guide".
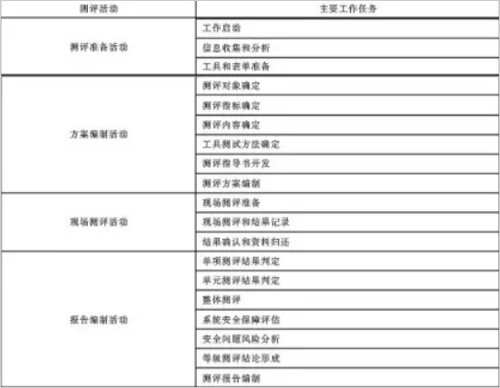
   Level evaluation process
It should be noted that the enterprise intranet information system, the cloud, or systems hosted elsewhere need to be evaluated. According to the principle of "who operates who is responsible, who uses who is responsible, who is responsible for who is responsible", the system responsibility subject is still Belong to the network operator, so do not be careless.
Waiting for insurance is just the beginning
At present, the recommended directory of national network security level protection evaluation agencies includes a total of 189 organizations. It should be noted that the security evaluation is not a security certification. There is no certification certificate. The evaluation report and record certification can only prove that the information system meets the security requirements of level protection. Meet the compliance needs of national laws and regulations.
The guarantee is only a basic requirement to ensure network security and information security. The basic guarantee is that the system can run smoothly, that is, the "bottom line". It does not mean that you can sit back and relax when you wait for security. Nor does it mean that you can wait for security. Legal sanctions can be circumvented when a risk incident occurs.
Meeting the demand for equal protection is only the first step to achieving network security and data security, and it is only the beginning of compliance. With the introduction of other regulations and measures, compliance requirements will inevitably become more stringent.
Steel Pipe Bending Machine,Tube Bending Machine,Pipe Bending Machine,Bending Machine
GUANGDONG CHITTAK INTELLIGENT EQUIPMENT CO.,LTD , https://www.ctklasercutting.com