Video surveillance platform software development status of <br> <br> video surveillance industry has gone through twenty years of development, today has a more complete and well-developed industry. With the development of video codec technology, from the analog era to the digital era, after experiencing the turbulence of H.263, MPEG4, and H.264 technologies, we finally ushered in the era of H.265, despite the current popularity. H.264. In this process, the video surveillance platform software has always played an indispensable role and played a major role. While promoting its own development, it also directly or indirectly promotes the codec technology, transmission technology, load balancing technology, and application technology. The promotion also satisfies the needs of a wide audience for monitoring shared functions.
Currently, in the context of very close integration of information technology and applications, the role of video surveillance platform software generally has two roles: one is the convergence of video and equipment management, the other is the sharing of resources and data applications. In the early development of the surveillance field, the first role dominated. This is an era of fortification and also a closed-loop era. Each video surveillance company has built its own market barriers by attacking cities in a low-competition, large-expansion climate. At this stage, most video surveillance manufacturers want to play their own characteristics and build their own domain on the original video codec and packaging technology. And the considerations for sharing (such as the harmonization of standards) are second only to that.
After experiencing such a "happy era of the Warring States Period," we ushered in an "empire age." In this era, I am afraid that most of the traditional video surveillance manufacturers are not so happy. First of all, the vast majority of people, to be exact, the majority of Internet users have progressed. In that happy era, video surveillance users were mostly “outsiders†who did not know how to operate and did not understand domain appeals and characteristics. Among them, there are old grandfathers who are all trembling with the mouse. There are also gimmicks who have just entered the field and who use video surveillance as a display platform or supporting role. Their requirements for monitoring the platform may only be able to look at the video and project it on the TV wall.
However, technology is advancing, and the industry is developing. After experiencing a period of unfathomable "unexplained" years, vast numbers of users quickly become familiar with monitoring software, thus creating a large number of "domain experts." They have a higher level of requirements for monitoring software, the video is not clear, how much bandwidth the transmission takes, the resolution, how long the storage, and so on, and the demand is more and more intense. On the other hand, each manufacturer can not dominate the world to occupy all areas of the market, in different areas, different market areas will have the requirements of resource sharing and interoperability, but also the development of software customization requirements. Especially in cities and provinces where Safe City is more developed, this requirement is very urgent. Whether it is possible to share video with heterogeneous systems of other manufacturers or whether it can be used to customize the development of some unique features of the units and fields has become an inevitable issue in this era.
ZNV ZTE strength video surveillance platform software development status
ZNV ZTE has been making video surveillance software one of its pillar products since its establishment in 1995. After experiencing the functional stage of video aggregation and device management, it has also embarked on the road to customizing domain requirements and sharing with other manufacturers' heterogeneous system resources.
However, ZNV's customer base has always been relatively broad. In addition to meeting the needs of operators and towers, *, transportation, electricity, education, railways, radio and television and other industries have involved. Of course, these industries are different in positioning and understanding of the video surveillance software platform, and the selection and use of software functions are also different. Some users use video surveillance as their main business, for example, the * field, map detection has become one of the four major detection methods, and due to the confidentiality mechanism within the industry, the sharing needs will be low, and further, others give Resources can, resources are harder for others. Some industry users regard the domain application as the main business, and video surveillance is only the auxiliary business. Other users, such as operators, are more inclined to exchange transmissions. They do not produce video. They are just video porters. In addition, for example, radio and television users, their requirements for video is to converge and share, providing channel set-top box channel material.
For many years, ZNV ZTE has been working on integration and has strong integration capabilities. As a result, ZNV's business forms are more diverse, meeting the functional needs, experience needs, and purchasing needs of different customer groups. Of course, as the onvif protocol is widely recognized in the field of domestic video surveillance and popularization of various national standards, integrated monitoring platform software like ZNV ZTE can offload some of the access pressure, but there are still a large number of non-standard monitoring. Devices and storage devices need to be accessed. For example, cloud storage devices, CMR devices, NVR devices, and even monitoring software platforms. Each of these hardware and software has its own characteristics. After being integrated, the users all hope to use the greatest value of each subsystem after integration. Due to the different functions, configurations, and usage methods of hardware and software products of various manufacturers, the complexity of integrated software customization will inevitably be caused.
In addition, as a standard in the field of industry, national standards are the most authoritative and are an entry threshold. The significance of its formulation is to allow users and constructors in the video surveillance or field to realize resources at the minimum cost. Sharing and interworking eliminate ambiguity between semantics to the greatest extent possible.
Customized software market development and key issues <br> <br> course customized software to meet the needs of most users for the field, but also caused some problems. From the developer's point of view, the coupling between software is too large, the stability and compatibility are poor, and the demand cannot be converged. From the user's point of view, problems such as inconsistent style, unstable and unsatisfied use of software, and gaps in expectations and implementation have always existed.
However, for the personalized needs of a large number of users and fields, software customization is inevitable and imperative. The emergence of a large number of customized video surveillance platform software on the market is proof. For example, in the * industry, the management of criminal investigation cases is not the same in all units, and the understanding of each software development company is also contending. In order to meet the convenience of the various units, they have to be customized and developed. If the model of the development model is not well designed, there may well be an awkward situation with a version of the code. There are also some issues that need to be resolved:
1. Stability issues Since customized software often adds a number of heterogeneous subsystems, cross-linking between systems requires coordination. However, the product levels of various manufacturers are uneven, and after being integrated, their stability is greatly reduced. For example, the SDK's access method is to integrate the third-party vendor's development package, so that the third-party modules run directly in their own process. Once the SDK has an illegal problem, it may cause the SDK's calling process to be illegal.
2. Maintenance issues The customization of software development and maintenance is a problem that has existed from beginning to end. The greater the degree of custom development, the greater the cost of maintenance and the higher the cost. At the same time, satisfying the business needs of different users requires developers to have a deeper knowledge of related fields, which, to a certain extent, also raises the threshold for the development of customized software and costs. It is hard to imagine that people who are not familiar with the field can develop excellent applications that meet the needs of the field.
3. Convergence of Requirements Customized software development is often a process in which demand and development go hand in hand. At the initial stage of software development, neither the user nor the acquirer of the demand often has the means to refine the requirements to the minimum granularity. This poses an obvious problem: the software developed does not match the needs of the user, or even differs greatly, resulting in the inability to converge. This is too common in custom software.
4. Software Security Issues This is not a problem with custom software but a problem with all software. The security of software mainly includes two aspects, network security and system security. In layman's terms, it is how to "defend the enemy outside the country" and how to "home-based combat." The surveillance equipment of a province's hall that appeared some time ago was invaded and controlled. In fact, it belongs to the first case. The manufacturer's coping strategy is mainly to strengthen the login password strength, etc. This approach is very thin for high-intensity intrusions.
So how can video surveillance platform software manufacturers find a balance between productization and customization? How can we increase the gold content of customized security software, especially management platform software? How can we no longer be vulnerable to problems and costs? In addition to the traditional management of demand management, iterative development and other management methods, I think the following points need to be complied with and explored:
1. Output diversity of video and session protocols:
In the field of video encoding and decoding, most of them currently comply with the MPEG4 standard, using the compression method of H.264, and H.265 is also in the ascendant. However, the packaging of video streams from various manufacturers is all-embracing. Some manufacturers are privately packaged, some are RTP packages, some are PS (program stream) packages, and some are TS (Transport Stream) packages. What's more, the compression method has also changed, which has caused great obstacles to the decoder and the sharing. At the same time, various fields have different regulations for the encapsulation of video streams. For example, in the field of *, due to the introduction of standards such as GB28181, the PS stream becomes the output standard; in the field of broadcasting and television, the set-top box generally requires the input TS stream to be decoded normally. There are also some industry standards, such as the railway industry, where the encapsulation of video streams is more flexible, RTP can be used, and RTP can be extended. The video stream compression method is not limited to H.264.
In order to adapt to the demands of video streaming in various fields, an excellent video surveillance platform software should be able to cope with this situation, at least not embarrassing. Then we require that we can output a variety of session specifications and video streams, including SIP-based (GB28181, GB28059, DB41, etc.), http-based, rtsp-based, RTMP-based, SNMP-based, Based on a customized specification and the like, the video stream needs to be compatible with PS streams and TS streams, as well as various packaged video streams. The diversity of the output of video and conversation protocols is achieved. When dealing with resource sharing demands, the cost of customized development will be reduced to a minimum.

The popular Hadoop framework and data warehouse provide a good engine for us to complete the work. The data is stored in the data warehouse and is used for deep mining and forecasting through the Hadoop system. It combines algorithms and models in the field of artificial intelligence, such as Bayesian classification, clustering, rough sets, and sequence patterns, to learn a lot of knowledge and use machines. The learning algorithm can establish certain mining rules so as to recursively improve mining rules and improve the accuracy and quality of mining. The large amount of such a large amount of data is undoubtedly a new functional growth driver for customized monitoring software, providing ample room for the expansion of custom software features.
3. Video surveillance platform software and Internet The traditional video surveillance system is basically running on a private network, that is, running in a local area network. The outflow and inflow of video data form a relatively closed loop. However, in today's resource sharing, apart from sending our own resources to other systems, we must allow the general public to enjoy the dividends of safe city construction in recent years. The most convenient way is to use the Internet.
In the Internet industry today, Youku, Tencent, Potato and other large-scale Internet video sites are rare for the integration of monitoring resources. Most of their resources are entertainment. When we drive a long way, how to avoid blocking and choosing the best route becomes the most warm service for the owner. It is easiest to complete these operations through the mobile phone or PC browser. Can this service be reflected in Youku or Tencent's video service menu? In addition to being embodied, how can we strengthen rich and varied interactions and increase the diversity of choices? This kind of benevolent person sees the needs of intellectuals and wise men, and I am afraid that only software platforms with deep customization and multiple session protocol output can be completed.
4. Video Surveillance Platform Software and Security Software As mentioned above, the security of software is not a problem unique to customized software but is a problem faced by all software products. In particular, how can customized video surveillance platform software enhance network security and system security? I think the following strategies can be taken:
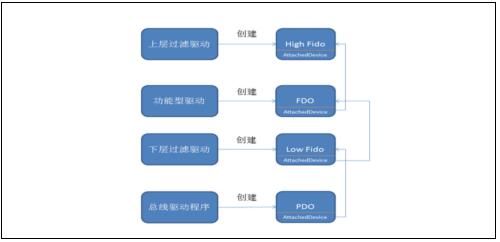
Network security: Traditional vendors generally adopt strategies such as adding firewalls, secure access gateways, and strengthening login authentication when dealing with network security. In addition, the method of adding filtering drivers can be used to deal with network security problems. Network traffic can be monitored and diverted in the network protocol stack driver. The TCPIP driver serves as the provider of the TDI (Transport Driver Interface) service, and the upper layer is the AFD (Auxiliary Function Driver), among which is TDI. Above AFD is the user-space socket library. You can add more drivers in the user space (ie, AFD), and you can add filter drivers in the TCPIP driver.
System security: System security mainly refers to system intrusion and anti-intrusion, virus detection and so on. It can generally be detected and dealt with by rootkit technology. For example, hooking system call descriptor table (SSDT), interrupt descriptor table (IDT), IPR processing function table, IAT (Import Address Table) of a specific process and other technologies. In addition, patching the calling process is a common practice. Through these means, the system functions or general procedure calls that are invoked can be effectively linked, registration of process calls can be realized, and combined with data analysis and machine learning methods, abnormal behavior and illegal processes in the system can be detected, which is in video surveillance. The field is also very meaningful.
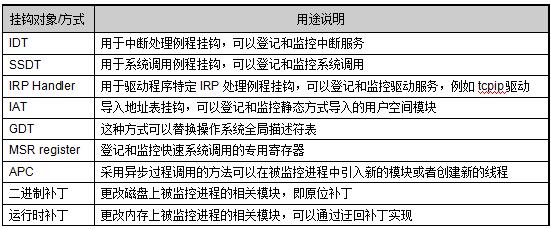
Table 4.2 Main methods of system security registration and monitoring under X86 architecture processor
Software customization future development trend
Software customization is in an important position in the development of the video surveillance management platform. It now exists and will exist for a long time to come. Its rise and fall are closely related to the development of various technologies in the monitoring industry and the advancement of monitoring methods. There are great opportunities and many problems. In the development of software customization, access and standardization, output flexibility and diversity can effectively reduce the cost of customization. In addition to traditional application programs, it is also possible to build a software protection system and a security registration system that integrates the operating system and application programs by taking over system services or adding filter-driven drivers, which is very effective for improving the security and robustness of customized software. significance. Of course, this also requires a higher technical threshold.
ZNV Zhongxing Liwei:
Shenzhen Zhongxing Force Technology Co., Ltd. (ZNV for short) is a leading comprehensive management solution provider. It has played a huge advantage in safety production and living, reducing energy consumption and improving efficiency, helping users establish safety. Operation and energy-saving and efficient integrated management system. The company's predecessor was ZTE's surveillance product line. In 1995, it began providing security services for the healthy operation of the communications network. In 2005, it officially operated independently. Headquartered in Shenzhen Hi-Tech Park, it has established R&D centers in Shenzhen, Nanjing, and Hangzhou. Its marketing service network covers 31 provinces and cities in China and over 70 overseas countries and regions, providing high-quality products and services to customers around the world.
Currently, in the context of very close integration of information technology and applications, the role of video surveillance platform software generally has two roles: one is the convergence of video and equipment management, the other is the sharing of resources and data applications. In the early development of the surveillance field, the first role dominated. This is an era of fortification and also a closed-loop era. Each video surveillance company has built its own market barriers by attacking cities in a low-competition, large-expansion climate. At this stage, most video surveillance manufacturers want to play their own characteristics and build their own domain on the original video codec and packaging technology. And the considerations for sharing (such as the harmonization of standards) are second only to that.
After experiencing such a "happy era of the Warring States Period," we ushered in an "empire age." In this era, I am afraid that most of the traditional video surveillance manufacturers are not so happy. First of all, the vast majority of people, to be exact, the majority of Internet users have progressed. In that happy era, video surveillance users were mostly “outsiders†who did not know how to operate and did not understand domain appeals and characteristics. Among them, there are old grandfathers who are all trembling with the mouse. There are also gimmicks who have just entered the field and who use video surveillance as a display platform or supporting role. Their requirements for monitoring the platform may only be able to look at the video and project it on the TV wall.
However, technology is advancing, and the industry is developing. After experiencing a period of unfathomable "unexplained" years, vast numbers of users quickly become familiar with monitoring software, thus creating a large number of "domain experts." They have a higher level of requirements for monitoring software, the video is not clear, how much bandwidth the transmission takes, the resolution, how long the storage, and so on, and the demand is more and more intense. On the other hand, each manufacturer can not dominate the world to occupy all areas of the market, in different areas, different market areas will have the requirements of resource sharing and interoperability, but also the development of software customization requirements. Especially in cities and provinces where Safe City is more developed, this requirement is very urgent. Whether it is possible to share video with heterogeneous systems of other manufacturers or whether it can be used to customize the development of some unique features of the units and fields has become an inevitable issue in this era.
ZNV ZTE strength video surveillance platform software development status
ZNV ZTE has been making video surveillance software one of its pillar products since its establishment in 1995. After experiencing the functional stage of video aggregation and device management, it has also embarked on the road to customizing domain requirements and sharing with other manufacturers' heterogeneous system resources.
However, ZNV's customer base has always been relatively broad. In addition to meeting the needs of operators and towers, *, transportation, electricity, education, railways, radio and television and other industries have involved. Of course, these industries are different in positioning and understanding of the video surveillance software platform, and the selection and use of software functions are also different. Some users use video surveillance as their main business, for example, the * field, map detection has become one of the four major detection methods, and due to the confidentiality mechanism within the industry, the sharing needs will be low, and further, others give Resources can, resources are harder for others. Some industry users regard the domain application as the main business, and video surveillance is only the auxiliary business. Other users, such as operators, are more inclined to exchange transmissions. They do not produce video. They are just video porters. In addition, for example, radio and television users, their requirements for video is to converge and share, providing channel set-top box channel material.
For many years, ZNV ZTE has been working on integration and has strong integration capabilities. As a result, ZNV's business forms are more diverse, meeting the functional needs, experience needs, and purchasing needs of different customer groups. Of course, as the onvif protocol is widely recognized in the field of domestic video surveillance and popularization of various national standards, integrated monitoring platform software like ZNV ZTE can offload some of the access pressure, but there are still a large number of non-standard monitoring. Devices and storage devices need to be accessed. For example, cloud storage devices, CMR devices, NVR devices, and even monitoring software platforms. Each of these hardware and software has its own characteristics. After being integrated, the users all hope to use the greatest value of each subsystem after integration. Due to the different functions, configurations, and usage methods of hardware and software products of various manufacturers, the complexity of integrated software customization will inevitably be caused.
In addition, as a standard in the field of industry, national standards are the most authoritative and are an entry threshold. The significance of its formulation is to allow users and constructors in the video surveillance or field to realize resources at the minimum cost. Sharing and interworking eliminate ambiguity between semantics to the greatest extent possible.
Customized software market development and key issues <br> <br> course customized software to meet the needs of most users for the field, but also caused some problems. From the developer's point of view, the coupling between software is too large, the stability and compatibility are poor, and the demand cannot be converged. From the user's point of view, problems such as inconsistent style, unstable and unsatisfied use of software, and gaps in expectations and implementation have always existed.
However, for the personalized needs of a large number of users and fields, software customization is inevitable and imperative. The emergence of a large number of customized video surveillance platform software on the market is proof. For example, in the * industry, the management of criminal investigation cases is not the same in all units, and the understanding of each software development company is also contending. In order to meet the convenience of the various units, they have to be customized and developed. If the model of the development model is not well designed, there may well be an awkward situation with a version of the code. There are also some issues that need to be resolved:
1. Stability issues Since customized software often adds a number of heterogeneous subsystems, cross-linking between systems requires coordination. However, the product levels of various manufacturers are uneven, and after being integrated, their stability is greatly reduced. For example, the SDK's access method is to integrate the third-party vendor's development package, so that the third-party modules run directly in their own process. Once the SDK has an illegal problem, it may cause the SDK's calling process to be illegal.
2. Maintenance issues The customization of software development and maintenance is a problem that has existed from beginning to end. The greater the degree of custom development, the greater the cost of maintenance and the higher the cost. At the same time, satisfying the business needs of different users requires developers to have a deeper knowledge of related fields, which, to a certain extent, also raises the threshold for the development of customized software and costs. It is hard to imagine that people who are not familiar with the field can develop excellent applications that meet the needs of the field.
3. Convergence of Requirements Customized software development is often a process in which demand and development go hand in hand. At the initial stage of software development, neither the user nor the acquirer of the demand often has the means to refine the requirements to the minimum granularity. This poses an obvious problem: the software developed does not match the needs of the user, or even differs greatly, resulting in the inability to converge. This is too common in custom software.
4. Software Security Issues This is not a problem with custom software but a problem with all software. The security of software mainly includes two aspects, network security and system security. In layman's terms, it is how to "defend the enemy outside the country" and how to "home-based combat." The surveillance equipment of a province's hall that appeared some time ago was invaded and controlled. In fact, it belongs to the first case. The manufacturer's coping strategy is mainly to strengthen the login password strength, etc. This approach is very thin for high-intensity intrusions.

Figure 3.1 Other major issues facing custom software
Should the need to change, to seize the high ground <br> <br> current market development, customized software in the field of popular video surveillance software for various industries growing, who wants to abandon the lofty software customized but outdated. The pursuit of software's productization blindly, trying to meet the needs of the product to meet the difficult audience, how much powerless. Customization software has such problems, but it is impossible to abandon it eagerly, not only can not abandon but there is still a growing reliance on the momentum, now buy a set of video surveillance platform software, if you do not add a little customization of the buyer's own desires are not going . So how can video surveillance platform software manufacturers find a balance between productization and customization? How can we increase the gold content of customized security software, especially management platform software? How can we no longer be vulnerable to problems and costs? In addition to the traditional management of demand management, iterative development and other management methods, I think the following points need to be complied with and explored:
1. Output diversity of video and session protocols:
In the field of video encoding and decoding, most of them currently comply with the MPEG4 standard, using the compression method of H.264, and H.265 is also in the ascendant. However, the packaging of video streams from various manufacturers is all-embracing. Some manufacturers are privately packaged, some are RTP packages, some are PS (program stream) packages, and some are TS (Transport Stream) packages. What's more, the compression method has also changed, which has caused great obstacles to the decoder and the sharing. At the same time, various fields have different regulations for the encapsulation of video streams. For example, in the field of *, due to the introduction of standards such as GB28181, the PS stream becomes the output standard; in the field of broadcasting and television, the set-top box generally requires the input TS stream to be decoded normally. There are also some industry standards, such as the railway industry, where the encapsulation of video streams is more flexible, RTP can be used, and RTP can be extended. The video stream compression method is not limited to H.264.
In order to adapt to the demands of video streaming in various fields, an excellent video surveillance platform software should be able to cope with this situation, at least not embarrassing. Then we require that we can output a variety of session specifications and video streams, including SIP-based (GB28181, GB28059, DB41, etc.), http-based, rtsp-based, RTMP-based, SNMP-based, Based on a customized specification and the like, the video stream needs to be compatible with PS streams and TS streams, as well as various packaged video streams. The diversity of the output of video and conversation protocols is achieved. When dealing with resource sharing demands, the cost of customized development will be reduced to a minimum.

Table 4.1 The existing mainstream video surveillance area interconnection and interoperability specifications
2. The video surveillance platform software and big data video monitoring software interfaced with so many devices and system resources. There are a large amount of data inflows and outflows at every moment. In addition to video streams, monitoring point alarm information, operation and maintenance data, and heterogeneous The domain knowledge of the platform formed a large-scale data group army. How to collect these data, each has its own tricks, but how to save and use these data is a new topic in the field of traditional security. The popular Hadoop framework and data warehouse provide a good engine for us to complete the work. The data is stored in the data warehouse and is used for deep mining and forecasting through the Hadoop system. It combines algorithms and models in the field of artificial intelligence, such as Bayesian classification, clustering, rough sets, and sequence patterns, to learn a lot of knowledge and use machines. The learning algorithm can establish certain mining rules so as to recursively improve mining rules and improve the accuracy and quality of mining. The large amount of such a large amount of data is undoubtedly a new functional growth driver for customized monitoring software, providing ample room for the expansion of custom software features.
3. Video surveillance platform software and Internet The traditional video surveillance system is basically running on a private network, that is, running in a local area network. The outflow and inflow of video data form a relatively closed loop. However, in today's resource sharing, apart from sending our own resources to other systems, we must allow the general public to enjoy the dividends of safe city construction in recent years. The most convenient way is to use the Internet.
In the Internet industry today, Youku, Tencent, Potato and other large-scale Internet video sites are rare for the integration of monitoring resources. Most of their resources are entertainment. When we drive a long way, how to avoid blocking and choosing the best route becomes the most warm service for the owner. It is easiest to complete these operations through the mobile phone or PC browser. Can this service be reflected in Youku or Tencent's video service menu? In addition to being embodied, how can we strengthen rich and varied interactions and increase the diversity of choices? This kind of benevolent person sees the needs of intellectuals and wise men, and I am afraid that only software platforms with deep customization and multiple session protocol output can be completed.
4. Video Surveillance Platform Software and Security Software As mentioned above, the security of software is not a problem unique to customized software but is a problem faced by all software products. In particular, how can customized video surveillance platform software enhance network security and system security? I think the following strategies can be taken:
Network security: Traditional vendors generally adopt strategies such as adding firewalls, secure access gateways, and strengthening login authentication when dealing with network security. In addition, the method of adding filtering drivers can be used to deal with network security problems. Network traffic can be monitored and diverted in the network protocol stack driver. The TCPIP driver serves as the provider of the TDI (Transport Driver Interface) service, and the upper layer is the AFD (Auxiliary Function Driver), among which is TDI. Above AFD is the user-space socket library. You can add more drivers in the user space (ie, AFD), and you can add filter drivers in the TCPIP driver.

Figure 4.1 Bus Drive as an Example to Add a Filter-Driven Schematic
System security: System security mainly refers to system intrusion and anti-intrusion, virus detection and so on. It can generally be detected and dealt with by rootkit technology. For example, hooking system call descriptor table (SSDT), interrupt descriptor table (IDT), IPR processing function table, IAT (Import Address Table) of a specific process and other technologies. In addition, patching the calling process is a common practice. Through these means, the system functions or general procedure calls that are invoked can be effectively linked, registration of process calls can be realized, and combined with data analysis and machine learning methods, abnormal behavior and illegal processes in the system can be detected, which is in video surveillance. The field is also very meaningful.

Table 4.2 Main methods of system security registration and monitoring under X86 architecture processor
Software customization future development trend
Software customization is in an important position in the development of the video surveillance management platform. It now exists and will exist for a long time to come. Its rise and fall are closely related to the development of various technologies in the monitoring industry and the advancement of monitoring methods. There are great opportunities and many problems. In the development of software customization, access and standardization, output flexibility and diversity can effectively reduce the cost of customization. In addition to traditional application programs, it is also possible to build a software protection system and a security registration system that integrates the operating system and application programs by taking over system services or adding filter-driven drivers, which is very effective for improving the security and robustness of customized software. significance. Of course, this also requires a higher technical threshold.
ZNV Zhongxing Liwei:
Shenzhen Zhongxing Force Technology Co., Ltd. (ZNV for short) is a leading comprehensive management solution provider. It has played a huge advantage in safety production and living, reducing energy consumption and improving efficiency, helping users establish safety. Operation and energy-saving and efficient integrated management system. The company's predecessor was ZTE's surveillance product line. In 1995, it began providing security services for the healthy operation of the communications network. In 2005, it officially operated independently. Headquartered in Shenzhen Hi-Tech Park, it has established R&D centers in Shenzhen, Nanjing, and Hangzhou. Its marketing service network covers 31 provinces and cities in China and over 70 overseas countries and regions, providing high-quality products and services to customers around the world.
Rigging Hardware Accessories,Stainless Steel Fully Threaded Eyebolts,Double Barrel Ferrule Aluminum Ferrule,Wire Rope Sleeve Double Barrel Ring
Taizhou Yuansheng Stainless Steel Products Co., Ltd. , https://www.ss-wirerope.com